The SEO community, in most part, first turned it's attention to the little green lock of HTTPS back in 2014, when Google published a post announcing HTTPS as a ranking signal. Almost immediately all SEOs advised their HTTP clients to move to HTTPS for ranking purposes, but in reality, it has never been (and never should have been) about rankings.
So why did Google talk about rankings? In short, to make people take notice.
The long-term goal for Google has been to make the web more secure for users and to protect their own users. After all, if Google presents a result to a user that will see them have their credit card details stolen they may be less trusting of Google to serve them safe, quality results.
HTTPS is again in the spotlight as Google Chrome 68 will actively highlight websites as "secure" and "not secure" to users. Therein lies the issue for me, the use of the word "secure".
Having an SSL certificate does not mean you have a secure website, and with the new European GDPR regulations fast approaching a lot of businesses may get caught out because of this misconception. High profile cyber attacks around the world have also given mass media spotlight to cybersecurity issues, with large brands (such as Barclays, a British multinational investment bank) launching public campaigns to raise awareness on cybersecurity basics.
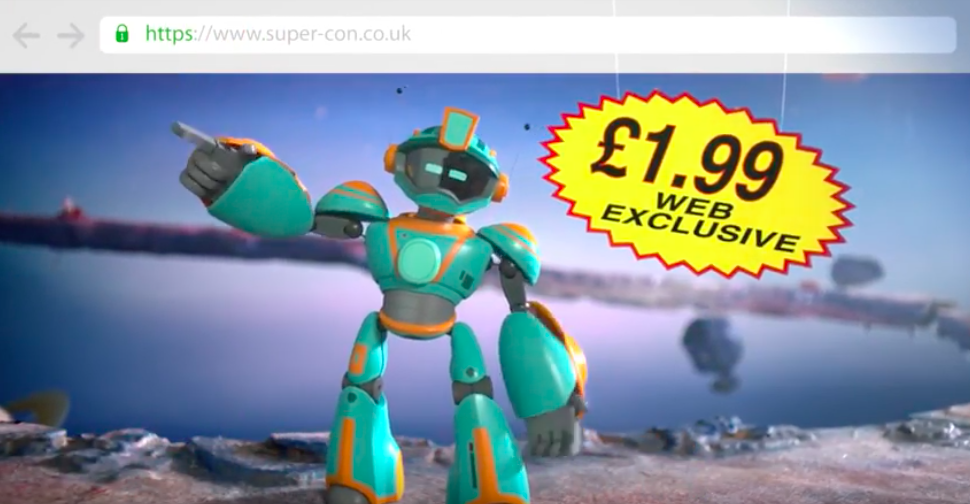 Barclay's "SuperCon" HTTPS campaign
Barclay's "SuperCon" HTTPS campaign
But, even this television advert from Barclays was wrong. It advertised that a site with a green lock and HTTPS is a sign that a website is genuine, and without one the website could be fake. Fake websites can still use HTTPS.
If a website, fake or genuine, wants to use SSL/TLS technologies, all they need to do is obtain a certificate. SSL certificates can be obtained for free and implemented in minutes through technologies such as Cloudflare, and as far as the browser is concerned - the site is secure.
Understanding How SSL Certificates Work
When a user navigates to a website, the website provides the certificate to the browser. The browser then validates that the certificate that has been provided by the website:
- Is valid for the same domain as the one being accessed.
- Has been issued by a trusted CA (Certificate Authority).
- Is valid and not passed its expiration date.
Once the user's browser has verified the validity of the SSL certification, the connection continues as secure. If not, you will get a not secure warning in your browser, or it will deny access to the site. If successful, the browser and website server exchange the necessary details to form a secure connection and the site loads.
So to what extent does HTTPS secure a website?
Encryption In Transit / Encryption At Rest
HTTPS (and SSL/TLS) provide what is called "encryption in transit". This means that our data and communications between a browser and website server (using a secure protocol) are in an encrypted format, so if these packets of data are intercepted, they cannot be read or tampered with.
However, when the browser receives the data it decrypts it, and when the server receives your data, it is also decrypted - so it can remembered in the future or used by other integrations, such as CRMs. SSL and TLS don't provide us with encryption at rest (when the data is stored on the website's server). This means that if a hacker is able to gain access to the server, they can read all the data you have submitted.
The majority of high profile hacks and data breaches come as a result of hackers gaining access to these unencrypted databases, so while HTTPS technologies mean our data gets to the databases securely, it isn't then being stored securely.
SSL Can Also Be Vulnerable
Like most technologies, SSL and TLS are ever evolving and being upgraded. SSLv1 was never publicly released, so the first real experience we all got with SSL came in 1995 with SSLv2, which contained a number of serious security flaws.
SSLv2 can still cause issues today, as a large number of current SSL implementations and configurations are incorrect meaning they are susceptible to DROWN attacks.
SSLv3 was introduced in 1996, and since then we have seen the introduction of TLSv1, TLSv1.1, and TLSv1.2.
This is where SSL itself can be a direct vulnerability. As technologies progress not all websites progress with them, and a lot of websites still support older protocols despite using a newer SSL certificate. Hackers can use this vulnerability and older support to perform a protocol downgrade attack - where they make the user browser reconnect to the website with an older protocol - and while a lot of modern browsers will prevent SSLv2 connections, SSLv3 is still more than 20 years old.
SSL itself is also vulnerable to a number of other potential attacks including BEAST, BREACH, FREAK, and Heartbleed.
HTTPS On Checkout/Login Pages Is A False Security
For a long time, a lot of e-commerce businesses maintained HTTPS only on checkout pages or user login pages but ran HTTP across other pages.
When you log in to a website the server sends back a cookie, this means you don't have to keep logging in and out of the site (it remembers you). The issue is then when you continue to browse the website on HTTP, the same authentication cookie is being sent and received over an unsecured connection, which could result in an attacker intercepting the cookie, stealing it, and then impersonating you at a later date.
In Conclusion
SSL/TLS, when implemented correctly, is a vital technology to secure user data when it is in transit between the user's browser and the website server. For full coverage, a website should also be using HSTS to protect against protocol downgrade attacks and cookie hijacking.
The technology also doesn't secure a website against thousands of other known hackable exploits, which can compromise user data.
Saying that HTTPS is secure isn't false, but it is also not strictly true. It is one piece in a cybersecurity jigsaw that is on the face of it one of the easiest security features to identify - especially from a web-crawler point of view. I have written previously about Google potentially adding a passive scanning element to an advanced web-crawler in the future, and factoring different aspects of website security into their ranking factors.
We need to educate our clients that they need to take more measures than just HTTPS to secure their websites and protect their users, as well as be GDPR compliant.
